Blogs
The Role of VAPT in Cybersecurity Defenses: Statistics and Risks
admin | 15 Sep 2023

As cyber threats become more sophisticated, protecting your business from data breaches and cyberattacks have never been more critical. Vulnerability Assessment and Penetration Testing (VAPT) is a crucial component of a comprehensive cybersecurity plan for businesses of all sizes. Just like how regular health checkups help us maintain our physical well-being, VAPT helps businesses assess their cybersecurity posture, identify vulnerabilities, and take the necessary steps to address them before attackers can exploit them.
The need for VAPT: Statistics on data breaches and leaks
The statistics on data breaches and leaks are alarming, with over 1,000 data breaches occurring in the first half of 2021 alone. The financial and reputational damage caused by these breaches can be significant, similar to how ignoring our physical health can lead to long-term consequences.
The COVID-19 pandemic has created new opportunities for cybercriminals, just like how a change in lifestyle can affect our health. The surge in remote work and online activity has made businesses more vulnerable to cyber threats.
The table provided displays a list of prominent data breaches that have occurred in recent years, highlighting the importance of having a strong cybersecurity plan in place, as such incidents can occur in every industry.
| Company Name | Year of Hack | Number of Records Breached | Type of Data Breached | Source of Reference |
|---|---|---|---|---|
| Tri Counties Bank | 2023 | Unknown | Identity documents, including passports and IDs. | American Banker |
| iD Tech | 2023 | Up to 1 million | Names, dates of birth, passwords, and emails. | TechCrunch |
| Saks Fifth Avenue | 2023 | Unknown | Unknown | TechRadar |
| Skylink CZ | 2023 | N/A | websites, customer systems and applications | Broadband TV News |
| Ferrari | 2023 | Unknown | Limited number of systems in IT environment compromised, customer data including names, addresses, email addresses, and phone numbers exposed | Car Dealer Magazine |
| General Bytes | 2023 | $1.5 million | Usernames, password hashes, and two-factor authentication | Crypto News Flash |
| DOCOMO Pacific | 2023 | Unknown | Some servers targeted, no damage to customer data, mobile network, or fiber services | KUAM News |
| Acer | 2023 | 160GB | 655 directories and 2,869 Confidential files | PCMag |
| Hospital Clinic de Barcelona | 2023 | Unknown | Computer systems, cancellation of 150 non-urgent operations and up to 3,000 patient checkups | ABC News |
| Flutterwave | 2023 | ?2.9 billion (~$6.9 million) | Account transfers | Techpoint Africa |
| AT&T | 2023 | 9 million | Basic personal information, device upgrade eligibility, number of lines on the account, devices used, installment agreement information | Cnet |
The IC3’s 2022 Internet Crime Report indicates that cybercrime is still a significant threat to both businesses and individuals, despite efforts to improve cybersecurity.
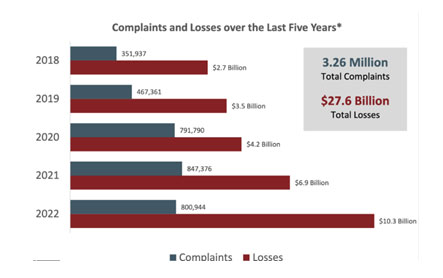
According to a recent report by Tenable, a cybersecurity firm based in Maryland, India suffered from the second-most tech exposure breaches in 2022 Healthcare and retail were the most frequently targeted industries, accounting for 11% of all breaches in India. The report also revealed that a significant number of security breaches were caused by outdated vulnerabilities and flaws, which raised the risk of breaches.
As Gartner predicts that cyber attackers will weaponize operational technology environments by 2025, it is essential to take a proactive approach to security. By implementing a cybersecurity network architecture, organizations can potentially decrease the financial impact of security incidents by an estimated average of 90% by 2024.
Overview of VAPT and its importance in cybersecurity
VAPT is an essential process that aims to ensure the health and security of their digital infrastructure. This thorough examination identifies any vulnerabilities in your IT systems, networks, and applications while assessing the effectiveness of existing security controls. By implementing firewalls, intrusion detection systems, antivirus software, and other security measures, you can protect your sensitive data and ensure business continuity
Moreover, it also involves staying up to date with the latest security trends, training employees on best practices for cybersecurity, and implementing policies and procedures to prevent and respond to cyberattacks. This ensures that your organization is always prepared to prevent and respond to cyber threats.
As cyber threats become increasingly sophisticated and regulations and compliance requirements grow more stringent, investing in information security and risk management services is becoming more crucial than ever. The market for security services is expected to witness an impressive growth of 11.3%, with spending projected to surpass $188.3 billion by 2023. This indicates that organizations are recognizing the value of protecting their digital assets and mitigating cyber risks.
By investing in VAPT services, organizations can better protect themselves against cyberattacks, data breaches, and other security incidents, minimizing their potential impact on operations, reputation, and financial health. Additionally, it is expected that increased expenditure will spur competition and innovation in the industry, leading to the creation of more advanced and effective solutions that work.
Types of Vulnerabilities and its Potential Impact
VAPT can help identify various types of vulnerabilities in IT infrastructure. These vulnerabilities can range from software flaws to network configuration errors, and they can pose a significant threat to the security and stability of an organization's IT assets.
| Types of vulnerabilities | Exploitability | Impact |
|---|---|---|
| Software Flaws | High | Unauthorized access, system failures, data breaches. |
| Configuration Errors | Low to medium | Data loss, network outages, and reputational harm |
| Authentication Flaws | Medium | Unauthorized access to data, privilege escalation, and reputational damage |
| Injection Flaws | High | Unauthorized access to sensitive data, data theft, and data destruction. |
| Cross-Site Scripting (XSS) | High | Sensitive data theft, unauthorized access, and website defacement |
| Cross-Site Request Forgery (CSRF) | High | Unauthorized transactions, data theft, and website defacement. |
| Denial of Service (DoS) | Medium-High | Network downtime, financial loss, and reputational damage. |
| Man-in-the-Middle (MitM) | High | Eavesdropping, sensitive information theft, malicious code injection into communication. |
| Session Hijacking | High | Data theft, unauthorized access, and website defacement. |
| Buffer Overflow | High | System crashes, data corruption, and unauthorized access. |
| XML external entity (XXE) | Medium | Exploitation of XML parser to gain unauthorized access. |
| Open Redirect | Medium | User redirection to a malicious site. |
| Server-Side Request Forgery (SSRF) | Medium | Sending request on behalf of the attacker. |
| Clickjacking | Low-medium | User clicking on hidden or disguised elements on a website. |
Note:
- Exploitability refers to the ease with which a vulnerability can be exploited by an attacker.
- Impact refers to the severity of the consequences if a vulnerability is exploited by an attacker.
From the table, it is evident that cyberattacks can cause financial loss, reputational damage, legal liabilities, and without VAPT services businesses are vulnerable to such attacks that can disrupt their operations and even force them to shut down.
Key Takeaways
Cybersecurity threats are getting more complex and sophisticated, necessitating the implementation of comprehensive safeguards. Simple cybersecurity measures are no longer enough, and frequent audits, such as VAPT checks, are required to identify vulnerabilities and weaknesses in your IT systems. You can significantly reduce the chance of a successful cyberattack and protect your valuable assets and sensitive information by prioritizing cybersecurity and conducting frequent VAPT assessments.
Furthermore, establishing a commitment to cybersecurity best practices via VAPT assessments can help organizations adhere to legal obligations and industry standards, foster stakeholder trust, and safeguard their reputations. With VAPT, you can protect your company right now and remain on top of evolving cyber threats.
Managed SOC to Boost Risk Mitigation Efficiency
15 Sep 2023
Overcoming IT Infrastructure Management Challenges with Managed IT Services
07 Sep 2023
Why Effective IT Infrastructure Management is Critical for Business Success
14 Aug 2023
Planning and Implementing ISO 27001: Best Practices and Common Challenges
18 Jul 2023
Terms of use | Privacy Policy | Contact us
© 2024 BhavyDigital. All Rights Reserved
Designed & Developed by Websoul Techserve


